I recently found myself grappling with a frustrating issue related to Remote Desktop Connection (RDP) on my Windows 11 machine. It all started when I realized that the system was automatically saving my credentials every time I connected to a remote computer. While this feature can be quite convenient, I started to question its security implications, especially given the sensitivity of the data I handle. My goal was to find a way to either enable or disable this credential-saving feature based on my needs.
My troubles began when I noticed that a colleague’s RDP setup was not saving credentials, which sparked my curiosity. I asked him how he achieved this, and he explained that it was all about tweaking the settings on the local machine. Intrigued, I decided to delve deeper into this topic, as I wanted to better control how and when my credentials were stored.
The first thing I did was check the settings within the Remote Desktop Connection application. I navigated to the RDP client by typing mstsc in the Windows search bar and hitting Enter. This opened the Remote Desktop Connection window. Under the “General” tab, I noticed an option to save credentials, which was currently checked. I unselected this box to prevent Windows from saving my credentials for future sessions. This change seemed straightforward, but I wasn’t sure if it was the ultimate solution or if other steps were necessary.
Next, I decided to explore the Windows settings to see if there were additional configurations I could adjust. I went to the Control Panel and looked for Credential Manager. Here, I found both “Web Credentials” and “Windows Credentials.” I checked the “Windows Credentials” section, where I saw that my RDP credentials were stored. I removed these entries to ensure that they wouldn’t be used in future connections.
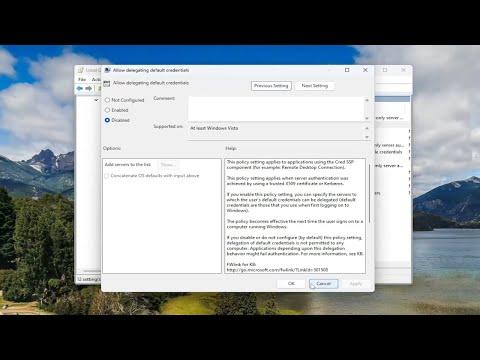
Despite these changes, I wanted to be absolutely certain that my credentials wouldn’t be saved in any scenario. So, I delved into the Group Policy Editor, which is a powerful tool for configuring advanced settings on Windows. To access it, I typed gpedit.msc in the Run dialog (accessible by pressing Win + R). Once inside, I navigated to the following path: Computer Configuration > Administrative Templates > System > Credentials Delegation. Here, I looked for settings related to Credential Delegation.
I found a policy called “Allow delegating saved credentials with NTLM-only server authentication.” By default, this was enabled, so I decided to disable it. This policy controls whether saved credentials can be used when connecting to servers that only use NTLM authentication. Disabling it seemed like a good precautionary measure. I also adjusted another related policy, “Allow delegating saved credentials,” to ensure that saved credentials were not used at all.
After making these adjustments, I rebooted my machine to apply the changes. I tested the Remote Desktop Connection again to see if the credentials were being saved. To my satisfaction, the system no longer stored my credentials. This adjustment provided a significant improvement in my control over security and ensured that my login information would not be saved inadvertently.
Throughout this process, I learned the importance of understanding the various layers of credential storage and management in Windows. The initial settings within the RDP client, coupled with changes in Credential Manager and Group Policy Editor, allowed me to tailor the system’s behavior to my specific needs. Whether I needed to enable or disable credential saving, I now felt more confident navigating these settings and making informed decisions about my system’s security.