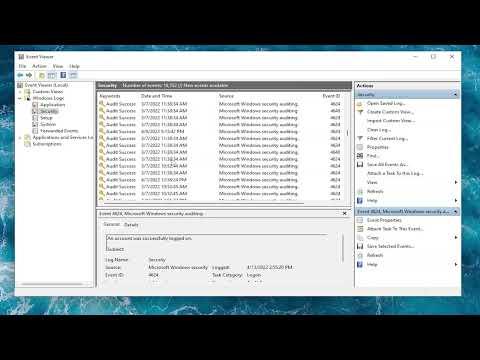
When I first needed to check user login history on my Windows 11/10 computer, I wasn’t entirely sure where to start. My goal was to track the login activities of different users on the system, whether to monitor usage patterns, troubleshoot login issues, or simply for security reasons. After some research and a bit of experimentation, I found a straightforward way to accomplish this using built-in tools. Here’s a detailed step-by-step guide on how I managed to check user login history on Windows 11/10.The first step in checking user login history is to access the Windows Event Viewer. The Event Viewer is a powerful tool that logs a wide array of system activities, including user logins. To begin, I pressed the Windows key and typed “Event Viewer” into the search bar. From the search results, I selected the Event Viewer application. Alternatively, I could also access it by pressing Win + R to open the Run dialog, typing eventvwr.msc, and hitting Enter.Once the Event Viewer was open, I navigated to the left pane and expanded the “Windows Logs” folder. Under this folder, I clicked on “Security.” This section contains a log of security-related events, including successful and failed login attempts.In the Security log, I looked for events with the ID 4624, which correspond to successful logins. To find these events, I used the “Filter Current Log” option in the right pane. I clicked on it, and a dialog box appeared where I could specify the event ID. I entered 4624 and clicked “OK” to apply the filter. This action filtered the log to show only the events related to successful user logins.To get detailed information about each login event, I double-clicked on a specific event. A new window popped up showing details about that particular login, including the date and time, the user account that logged in, and the workstation or device used. The “Account Name” field provided the username, while the “Logon Type” field indicated the type of login (e.g., interactive logon, network logon).In addition to successful logins, I also wanted to check for failed login attempts. To do this, I returned to the “Filter Current Log” option and added another filter for event ID 4625. Event ID 4625 corresponds to failed login attempts. After applying this filter, I was able to see a list of failed login attempts, which included details like the reason for the failure and the username involved.To get a comprehensive view of all login activities, I combined the results from both event IDs. By carefully examining the logs, I could assess both successful and failed login attempts, identify any unusual patterns, and pinpoint any potential security concerns.Another useful feature of the Event Viewer is the ability to export log data. If I needed to share the login history with someone or keep a record for future reference, I could easily export the filtered log. To do this, I selected “Save All Events As…” from the right pane. I chose the format I wanted (such as .evtx or .csv), specified the file name and location, and clicked “Save.” This feature proved handy for maintaining records or conducting further analysis.While the Event Viewer provided a detailed view of login events, I also explored other methods to get a summary of user logins. One such method involved using the command line. I opened Command Prompt with administrative privileges by right-clicking the Start button and selecting “Command Prompt (Admin)” or “Windows Terminal (Admin).” In the Command Prompt window, I entered the command wmic netlogin list to get a list of user login activities. This command provided a summary of login information but lacked the depth and detail found in the Event Viewer logs.For users looking for a more user-friendly interface, third-party tools are available that can provide an overview of login activities. These tools often offer additional features like graphical reports and easier navigation. However, I preferred using the built-in Event Viewer as it provided all the necessary details without the need for additional software.As I continued to use these methods to monitor user logins, I realized the importance of regularly checking login history for maintaining system security. Monitoring login activities helped me detect any unauthorized access attempts and ensure that only authorized users were accessing the system.In summary, checking user login history in Windows 11/10 is a straightforward process with the help of the Event Viewer. By filtering for specific event IDs, I was able to track successful and failed login attempts, view detailed information about each event, and export the logs if needed. For those looking for additional options, command-line tools and third-party software can provide supplementary features. Regularly reviewing login history is a crucial practice for ensuring the security and proper management of a Windows system.
How to Check User Login History in Windows 11/10 [Tutorial]